- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I have been pouring over the documentation over the past few days but to no avail and would really appreciate some help.
I am working on an Ionic project that would call the Visa Forex API ie "https://sandbox.api.visa.com/forexrates/v1/foreignexchangerates".
Due to CORS, I am using the Ionic proxy to proxy my requests but whenever I make the request I get:
{"status":400,"code":"9124","severity":"ERROR","message":"Expected input credential was not present","info":""}}
The body of the request:
"cardAcceptor": {
"address": {
"city": "Foster City",
"country": "RU",
"county": "San Mateo",
"state": "CA",
"zipCode": "94404"
},
"idCode": "ABCD1234ABCD123",
"name": "ABCD",
"terminalId": "ABCD1234"
},
"destinationCurrencyCode": "840",
"markUpRate": "1",
"retrievalReferenceNumber": "201010101031",
"sourceAmount": "100",
"sourceCurrencyCode": "643",
"systemsTraceAuditNumber": "350421",
}
The request headers:
- Accept:application/json
- Accept-Encoding:gzip, deflate, br
- Accept-Language:en-US,en;q=0.9,zh-CN;q=0.8,zh;q=0.7
- Authorisation:Basic QUxUUVJTR0o5R1FGMTI2TjEyQTYyMVYtTzEwTWE0WDJjT1VTNjZMMzJIZkFiWDg1VTpQMzk3ZzVQazhFWDlwMjd4RjF5VzFDakI3ODh0U21r
- Connection:keep-alive
- Content-Length:357
- Content-Type:application/json
- Cookie:io=YlZBEislSYOtVnlDAAAD; JSESSIONID=7e72dfab6a8afff3f550deeb6f85; treeForm_tree-hi=treeForm:tree:applications:ExperienceSystem
- Host:localhost:8100
- Origin:http://localhost:8100
- Referer:http://localhost:8100/home
- User-Agent:Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/75.0.3770.100 Safari/537.36
The response header:
- Access-Control-Allow-Origin:*
- cache-control:no-cache, no-store, must-revalidate
- connection:close
- content-length:132
- content-type:application/json;charset=UTF-8
- date:Sat, 22 Jun 2019 03:52:54 GMT
- expires:-1
- pragma:no-cache
- server:nginx
- set-cookie:ak_bmsc=5C170ACBCAC2130EAB1F261D56D984D7686746B4D52D000016A60D5DD41D7D57~plqhFNZXkEgoRQuQjoqVGsWRkyUiLyTZVbCviPV6M8cBETzPmKTk+iLJC0jYJbeAyyEdboWa/UVfRxY9+lf5flv7EqMym8VNmquQDyyV9RV99cT99leGMIG2o8yiDwqMfIGLm8akuFZNExL5MCi1zmBAnd2Fx+hqjFlGdzZq8bDrXBDx/4yY1/PCFu9F2aRtfHkbr2RgzjJ0DDSICmiDr1kQhR6vXasGtiJliPzgVvozs=; expires=Sat, 22 Jun 2019 05:52:54 GMT; max-age=7200; path=/; domain=.api.visa.com; HttpOnly
- strict-transport-security:max-age=2592000;includeSubdomains
- x-app-status:401
- x-content-type-options:nosniff
- x-correlation-id:1561175574_394_863963202_l55c014_VDP_WS
- x-frame-options:SAMEORIGIN
- X-Powered-By:Express
- x-served-by:l55c014
- x-vdp-authn-api-visa-id:FX.100
- x-vdp-normalized-url:/forexrates/v1/foreignexchangerates
- x-xss-protection:1; mode=block
My proxy file settings in the Ionic project, proxy.conf.js:
const fs = require('fs');
const PROXY_CONFIG = {
"/api": {
target: {
"host": "sandbox.api.visa.com",
"protocol": "https:",
"path": "/forexrates/v1/foreignexchangerates",
"key": fs.readFileSync("C:\\Users\\username\\Desktop\\privateKey.pem"),
"cert": fs.readFileSync("C:\\Users\\username\\Desktop\\cert.pem"),
"ca": fs.readFileSync("C:\\Users\\username\\Desktop\\DigiCertGlobalRootCA.cer")
},
changeOrigin: true,
secure: false
}
};
module.exports = PROXY_CONFIG;
Any help is greatly appreciated!
Thank you
Solved! Go to Solution
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Always getting "Expected input credential was not present" error
Hey @boav_rum,
So I tested with the request payload you provided and I got a successful 200 OK response. Your request payload is surely correct (please scroll down to see the correct Request, Response, and Response Header that gets 200 OK results).
The error 400 - 9124 Expected input credential was not present usually occurs when the credentials used are invalid. Can you please confirm if you are using valid credentials?
To access your project credentials, please login to your VDP account > My Account > Dashboard > project app > Credentials
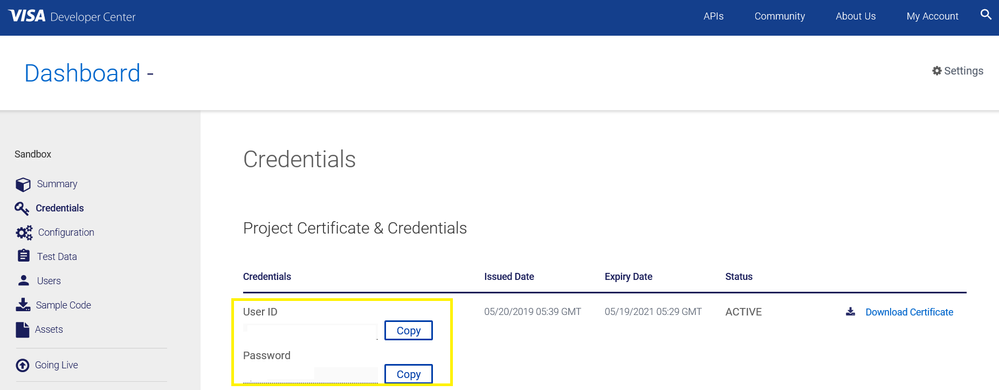
Also, please double check the SSL settings and make sure the keystore has all the necessary certificates imported. To start, this error usually occurs when your certificates are not sent.
· Keystore is not setup. Certificates are not in the keystore:
○ For java keystore (jks) run keytool command and verify all the certificates have been imported on the keystore
· keytool -list -v -keystore keystore.jks
○ For a p12 execute the following openssl command:
· openssl pkcs12 -info -in keyStore.p12
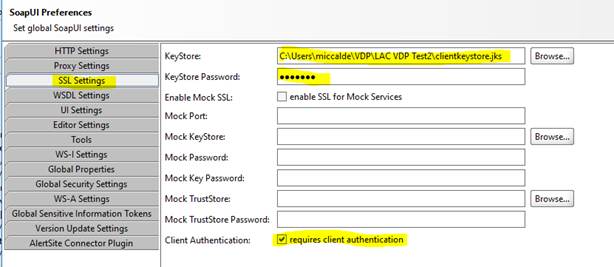
· In SOAPUI check File->Settings->SSL Settings and make sure the KeyStore and KeyStore Password are populated in Soap UI
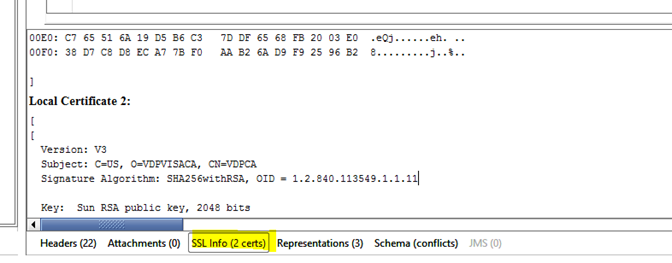
· Check SSL Info Tab in SOAP UI Response and verify you have a Local Certificate 1, Local Certificate 2 followed by Peer Certificate 1 and Peer Certificate 2
· In addition to that, if you are using SOAP UI, please make sure to select "Authenticate pre-emptively" under "Auth (Basic)" tab. Also, please double check in the request raw tab that the "Authentication Basic" is present.
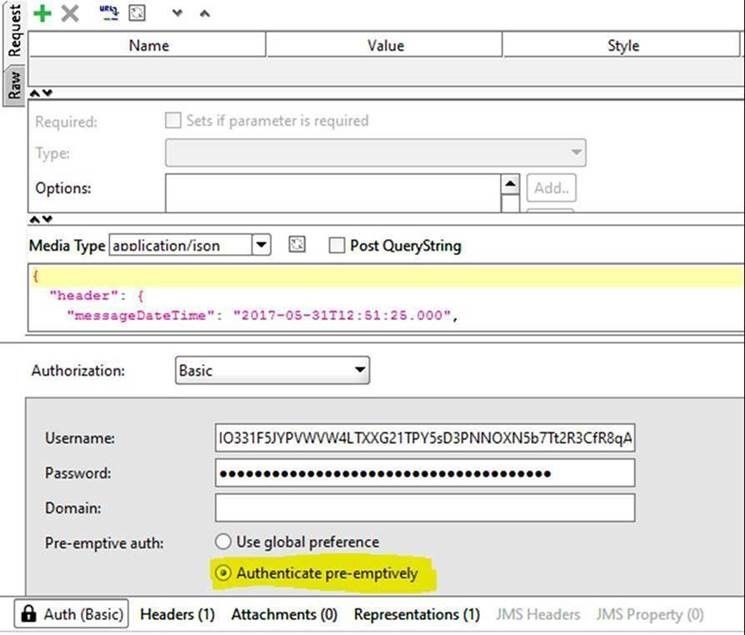
· Check request header and make sure Authorization: Basic has been populated with the base64 encoded username and password:
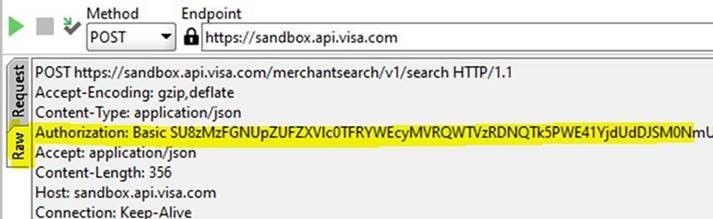
Please follow the Working with Visa APIs guide and read the Two-Way SSL (Mutual Authentication) guide: https://developer.visa.com/pages/working-with-visa-apis/two-way-ssl
Furthermore, please make sure you are using valid Test Data from your project app.
If the issue persists, please provide more information on the error you have received for further investigation. Please send the response request of the error received, screenshot and the Correlation ID. Please let us know if you have other questions.
Below are the steps to get the Correlation ID using a Google Chrome browser.
1>Open Chrome menu.
2>Click on More tools then Developer tools.
3>Check the box to Preserve Log for the Network Tab.
4>Then try to click on the add API link.
5>You can find the Correlation ID in the network log for add API call.
Additional Note:
Request:
{
"systemsTraceAuditNumber": "350421",
"destinationCurrencyCode": "840",
"cardAcceptor": {
"address": {
"country": "RU",
"zipCode": "94404",
"city": "Foster City",
"county": "San Mateo",
"state": "CA"
},
"idCode": "ABCD1234ABCD123",
"name": "ABCD",
"terminalId": "ABCD1234"
},
"markUpRate": "1",
"sourceAmount": "100",
"retrievalReferenceNumber": "201010101031",
"sourceCurrencyCode": "643"
}
Response:
{
"originalDestnAmtBeforeMarkUp": "1.65",
"markUpRateApplied": "1.0",
"conversionRate": "0.01650000",
"destinationAmount": "1.63"
}
Response Header:
Status Code: 200 OK
Server : nginx
Content-Type : application/json
Content-Length : 122
X-SERVED-BY : l55c012
X-CORRELATION-ID : 1561181131_570_840006861_l55c012_VDP_WS
X-Backside-Transport : OK OK,OK OK
X-APP-STATUS : 200
X-Global-Transaction-ID : de8c0d945d0dbbcb0a4c8ba9
X-Frame-Options : SAMEORIGIN
X-XSS-Protection : 1; mode=block
X-Content-Type-Options : nosniff
Strict-Transport-Security : max-age=2592000;includeSubdomains
Cache-Control : no-cache, no-store, must-revalidate
Pragma : no-cache
Expires : -1
Date : Sat, 22 Jun 2019 05:25:32 GMT
Connection : keep-alive
Thanks,
Diana
Was your question answered? Don't forget to click on "Accept as Solution" to help other devs find the answer to the same question.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Always getting "Expected input credential was not present" error
Hey,
So I have actually tried it with Postman and it works fine, setting up the certificates as shown:
CRT file-> C:\Users\username\Desktop\cert.pem
Key file-> C:\Users\username\Desktop\privateKey.pemAnd because I am getting an "Expected input credential was not present" rather than an "Incorrect credential" error leads me to think that the certificates are not being sent?
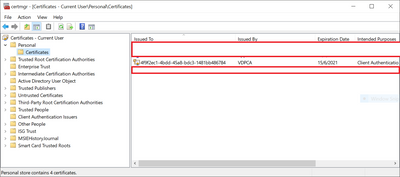
However, I am pretty sure I have installed the certificate necessary. Please refer to the below picture of my cert store (its the one issued by VDPCA right?).
Could you explain what "openssl pkcs12 -info -in myP12File.p12" does? I have done it but am still facing this error. Do I need to refer to it somewhere in the code? Additionally, I have tried deploying onto an Android phone so that I do not have to go through a proxy but I am facing the same error as well. You can take a look at the screenshot below.
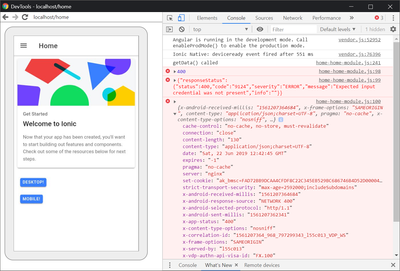
I aim to make use of the Forex RatesAPI to provide a convenience feature but for now, I am still simply trying out the API to get a hang of it.
Please let me know if you need any more information!
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Always getting "Expected input credential was not present" error
Hi @boav_rum,
To add the DigiCert Global Root CA certificate, download it from your VDP Project. Refer to screenshot below.
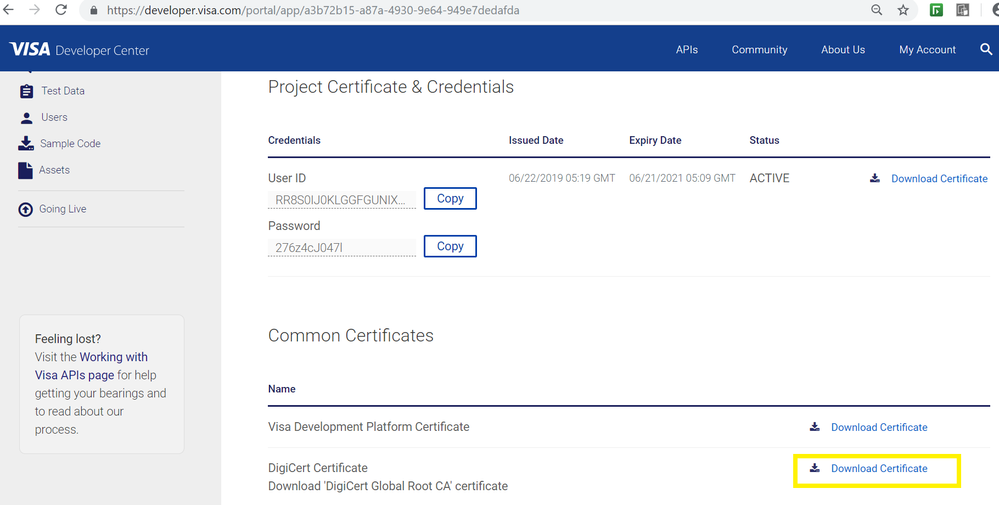
Once downloaded, you will need to convert the DigiCert Global Root CA certificate from Binary format to Base64 format.
You can do this by using Windows Certificate Management:
Windows Certificate Management
- Double-click on the DigiCertGlobalRootCA.crt file to open it into the certificate display.
- Select the Details tab, then select the Copy to file button.
- Click Next on the Certificate Wizard.
- Select Base-64 encoded X.509 (.CER), then Next.
- Select Browse (to locate a destination) and type in the filename DigiCertGlobalRootCA.
- Click Save. You now have the file DigiCertGlobalRootCA.cer
Then, run the following keytool command to add it to your truststore.
C:\Users\dtranyee\Documents\Test Project\20190621 Foreign Exchange Rates test1>keytool -import -alias DigiCertGlobalCA -file DigiCertGlobalRootCA.crt -storetype JKS -keystore clientkeystore.jks
After you hit "Enter" you will see the Command Prompt have the following output:
Enter keystore password:
Owner: CN=DigiCert Global Root CA, OU=www.digicert.com, O=DigiCert Inc, C=US
Issuer: CN=DigiCert Global Root CA, OU=www.digicert.com, O=DigiCert Inc, C=US
Serial number: 83be056904246b1a1756ac95991c74a
Valid from: Thu Nov 09 16:00:00 PST 2006 until: Sun Nov 09 16:00:00 PST 2031
Certificate fingerprints:
MD5: 79:E4:A9:84:0D:7D:3A:96:D7:C0:4F:E2:43:4C:89:2E
SHA1: A8:98:5D:3A:65:E5:E5:C4:B2:D7:D6:6D:40:C6:DD:2F:B1:9C:54:36
SHA256: 43:48:A0:E9:44:4C:78:CB:26:5E:05:8D:5E:89:44:B4:D8:4F:96:62:BD:26:DB:25:7F:89:34:A4:43:C7:01:61
Signature algorithm name: SHA1withRSA
Subject Public Key Algorithm: 2048-bit RSA key
Version: 3
Extensions:
#1: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 03 DE 50 35 56 D1 4C BB 66 F0 A3 E2 1B 1B C3 97 ..P5V.L.f.......
0010: B2 3D D1 55 .=.U
]
]
#2: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen:2147483647
]
#3: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_CertSign
Crl_Sign
]
#4: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 03 DE 50 35 56 D1 4C BB 66 F0 A3 E2 1B 1B C3 97 ..P5V.L.f.......
0010: B2 3D D1 55 .=.U
]
]
Trust this certificate? [no]: yes
Certificate was added to keystore
Warning:
The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore clientkeystore.jks -destkeystore clientkeystore.jks -deststoretype pkcs12".
C:\Users\dtranyee\Documents\Test Project\20190621 Foreign Exchange Rates test1>
Next, to add the root certificate to your clientkeystore.jks file (Note: I named my .jks filename to be "clientkeystore.jks" and it's in the same folder as my public and private key. After downloading the VDPCA-SBX.pem file I put it in the same folder) place the VDPCA-SBX.pem file into your project app folder where the public and private key are (please refer to screenshot below for my project folder).
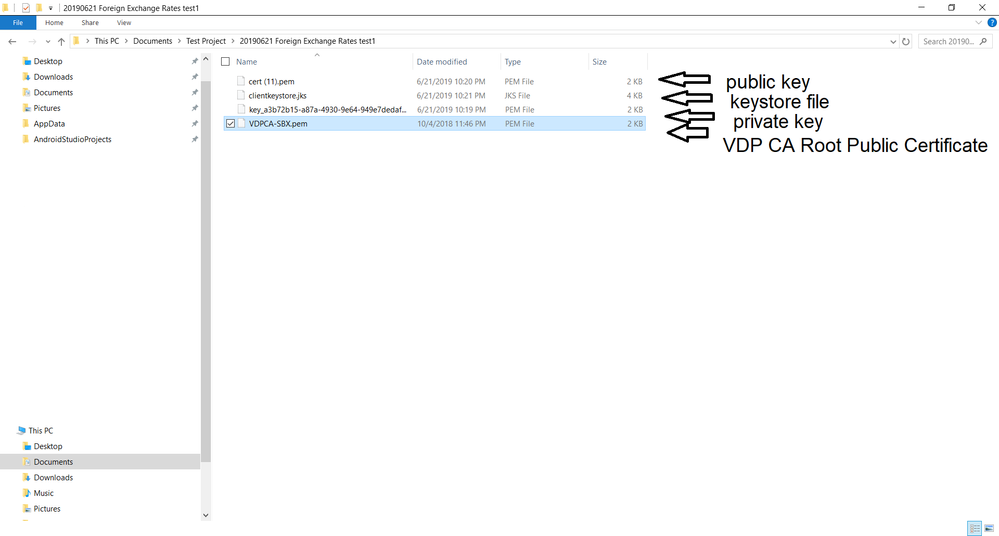
Using the Command Prompt, I ran the command below to add the VDP CA Root Public Certificate to the keystore:
keytool -import -alias ejbca -keystore clientkeystore.jks -file VDPCA-SBX.pem -storepass abcdef
After running the command above, this is what I will see in my command prompt.
Command Prompt Output:
C:\Users\dtranyee\Documents\Test Project\20190621 Foreign Exchange Rates test1>keytool -import -alias ejbca -keystore clientkeystore.jks -file VDPCA-SBX.pem -storepass abcdef
Owner: C=US, O=VDPVISACA, CN=VDPCA
Issuer: C=US, O=VDPVISACA, CN=VDPCA
Serial number: 2d1ed295f96ad97a
Valid from: Thu Jul 23 21:27:37 PDT 2015 until: Sun Jul 20 21:27:37 PDT 2025
Certificate fingerprints:
MD5: 86:73:94:83:49:00:9D:82:CF:A0:BD:FE:F2:E3:95:F3
SHA1: A9:30:33:1C:EC:50:7C:71:60:51:4E:03:FF:9E:C1:CA:E6:FE:EC:C4
SHA256: 8D:65:FA:35:59:FD:C3:43:F0:E6:F0:DF:AB:03:DE:49:F3:76:14:20:22:69:C4:B2:56:1A:AC:24:07:7B:C1:F6
Signature algorithm name: SHA256withRSA
Subject Public Key Algorithm: 2048-bit RSA key
Version: 3
Extensions:
#1: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: AF DD 6E B6 A0 4B 9C 79 B9 16 08 62 E6 23 31 10 ..n..K.y...b.#1.
0010: A7 82 EB A1 ....
]
]
#2: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen:2147483647
]
#3: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_CertSign
Crl_Sign
]
#4: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: AF DD 6E B6 A0 4B 9C 79 B9 16 08 62 E6 23 31 10 ..n..K.y...b.#1.
0010: A7 82 EB A1 ....
]
]
Trust this certificate? [no]: yes
Certificate was added to keystore
Warning:
The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore clientkeystore.jks -destkeystore clientkeystore.jks -deststoretype pkcs12".
C:\Users\dtranyee\Documents\Test Project\20190621 Foreign Exchange Rates test1>
Then afterwards, you can try to test with SoapUI for Foreign Exchange Rates and you will get a successful 200 OK response (refer to SoapUI Foreign Exchange Rates screenshot below. I got a 200 OK response. Multiple screenshots of SoapUi show that I'm scrolling right to see the successful Response).
For instructions on how to setup SoapUI for Two-Way (Mutual SSL) please go here - https://developer.visa.com/pages/working-with-visa-apis/two-way-ssl
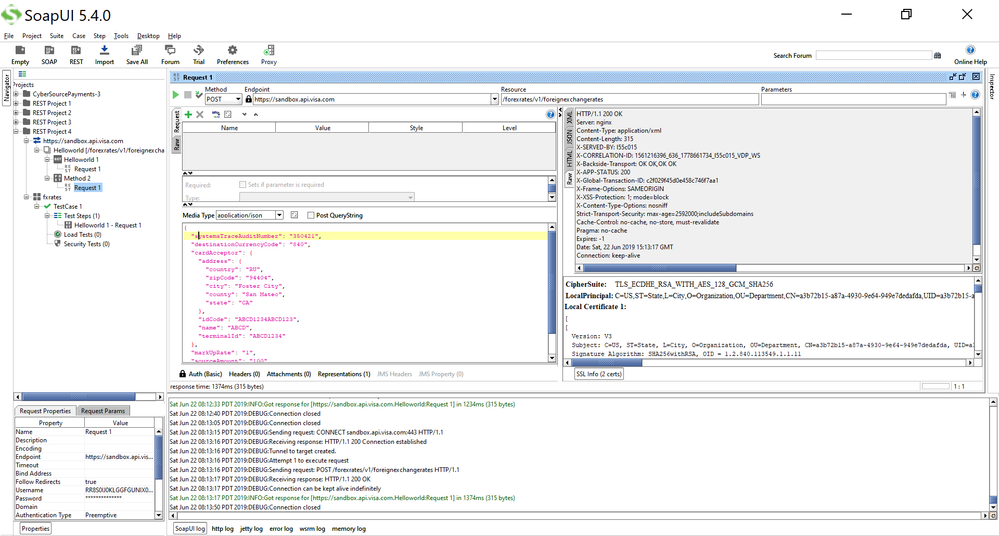
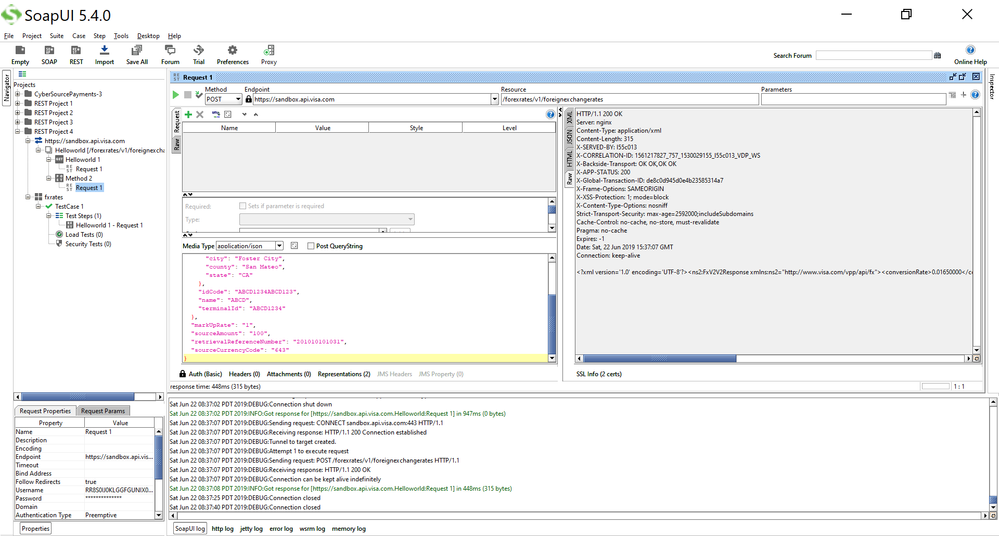
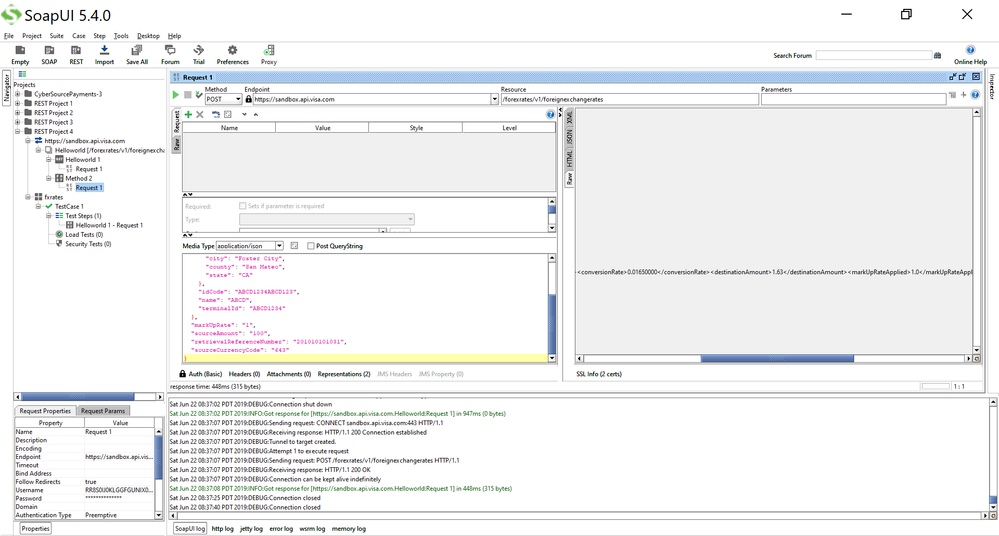
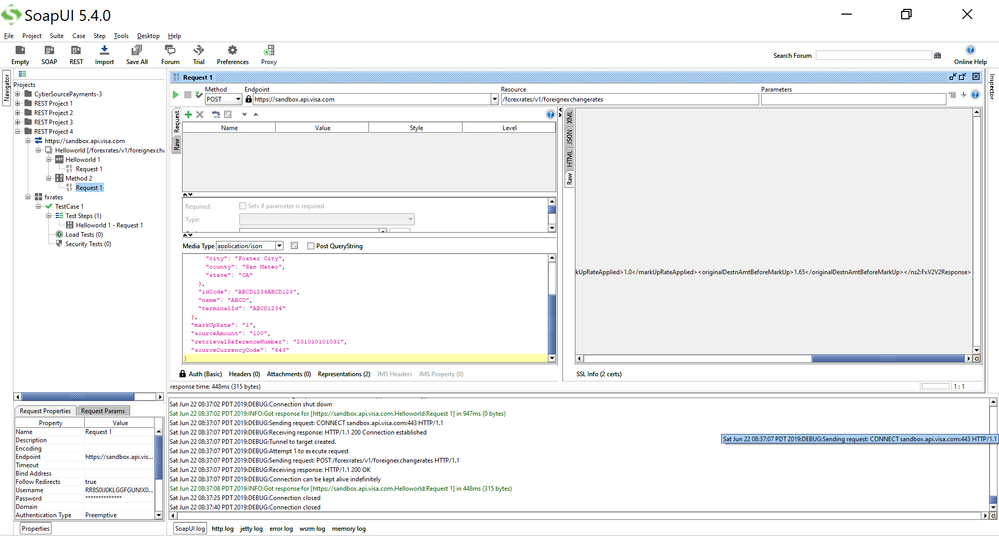
You can also see the successful response in SoapUI XML format:
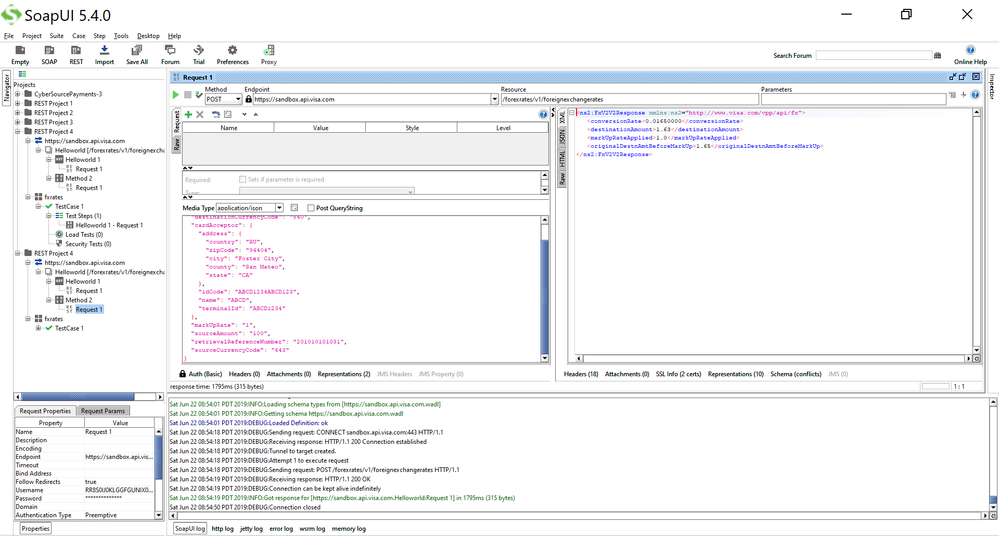
Hope that helps and hope you're having a happy day!
Thanks,
Diana
Was your question answered? Don't forget to click on "Accept as Solution" to help other devs find the answer to the same question.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Always getting "Expected input credential was not present" error
I followed your guide but i am not getting anything in the test data step. What could have gone wrong here?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Always getting "Expected input credential was not present" error
Hi @mantis07,
When you say that you are not getting anything in the test data step, can you please explain what it is that you do not understand?
I'll provide more clarification in this forum thread for you, to further your understanding of the Test Data topic.
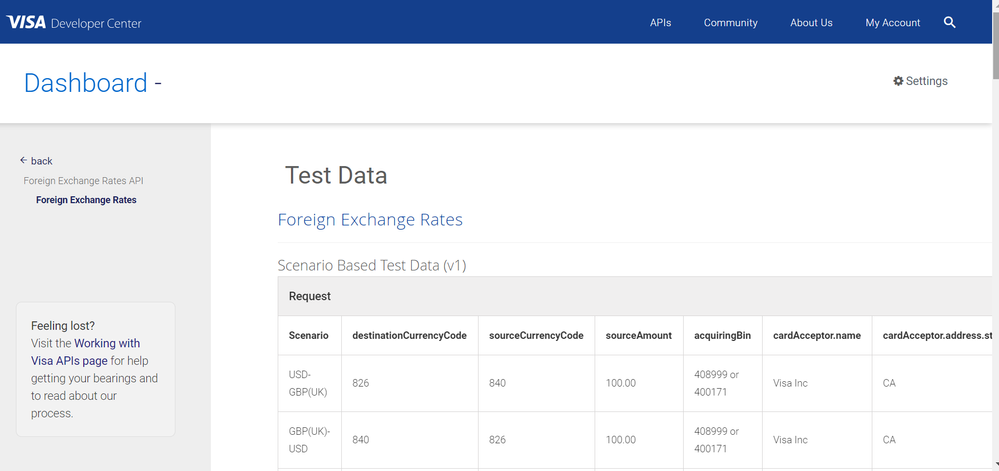
When you create a test App in our sandbox you will receive test data in your App. The test data for your Visa Developer application is available in the Dashboard under test data in the left navigation, this will ensure that you are using valid data that has been provisioned for specific scenarios. You will basically have a table per API that is split into the Request and Response sections and the values on the Request section are meant to be populated in the payload with the intention of obtaining results specified in the Response section.
Sandbox data is limited to what is provided in the Test Data tables and is not integrated to the Visa Network and you cannot test real data in sandbox.
Thanks,
Diana
Was your question answered? Don't forget to click on "Accept as Solution" to help other devs find the answer to the same question.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Always getting "Expected input credential was not present" error
Hey,
Apologies for the late reply. I have created and added the CA (DigiCertGlobalRootCA.cer) and Visa (VDPCA-SBX.pem) certificates to the clientkeystore.jks file but would like to just ask: where do I make use of the private and public keys of my project now? Do I need to import them to the keystore as well?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @boav_rum,
Please follow the Two-Way SSL guide step-by-step and in its specific order. The guide is here - https://developer.visa.com/pages/working-with-visa-apis/two-way-ssl#
From the guide, I have compiled some information for you to take a look at as it relates to your question.
To establish a Two-Way SSL (Mutual Authentication) connection, you must have the following:
* private key
* client certificate
* certificate authority root certificate, and
* certificate authority intermediate certificates (Note: These certificates are optional for the Visa Developer sandbox)
You will need to obtain a private key, client certificate, and certificate authority root certificate. You will also learn about how to bundle the certificates into keystores, using Java keytool or OpenSSL.
The process of creating the CSR yields the CSR file itself and also a private key (which corresponds to a public key, which is encoded into the CSR file). There are multiple tools that you can use to create a CSR, such as Java keytool or OpenSSL. Both tools are available for free to download from the Internet for all major operating systems.
Configuring a Two-Way SSL Keystore Using an Auto-generated CSR
Visa Developer creates the CSR file and submits the CSR to itself. The output of this process is the private key and the certificate of the client.
Depending on the APIs you select, click on either Submit a Certificate Signing Request or Generate a CSR for Me.
Visa Developer self-submits a certificate request and produces a .pem file with the private key of your certificate in it.
Note: Once you complete the project creation process, Visa Developer Platform (VDP) will provide you with the links of the certificates to download. In this case, Visa Developer provides a VDP CSR. Once you obtain the private key and the certificates, you can begin to create the key stores and start testing mutual SSL connectivity.
Configuring a Two-Way SSL Keystore Using an Auto-generated CSR
The following steps include examples for context.
1.Place your private key file (for example: privateKey.pem) and your certificate file from VDP (for example: cert.pem) in the same directory. Generate a keystore (for example: myProject_keyAndCertBundle.p12) file as shown below.
> openssl pkcs12 -export -in cert.pem -inkey "privateKey.pem" -certfile cert.pem -out myProject_keyAndCertBundle.p12
Note: The myProject_keyAndCertBundle.p12 is only a placeholder file name. You may choose to name it anything else.
2.If you need a Java Key Store, run the following Java keytool command to convert your P12 file into a JKS file.
> keytool -importkeystore -srckeystore myProject_keyAndCertBundle.p12 -srcstoretype PKCS12 -destkeystore myProject_keyAndCertBundle.jks
3.Run the following Java keytool command to validate the contents of your new JKS file.
> keytool -list -v -keystore myProject_keyAndCertBundle.jks
4.Run the following command to add the root certificate to your JKS file.
> keytool -import -alias ejbca -keystore myProject_keyAndCertBundle.jks -file VDPCA-SBX.pem -storepass <password>
To generate a CSR using keytool:
1.Generate a keystore file that contains public/private key pair (for example: 'clientkeystore.jks'), as shown below, using RSA, a keysize of 2048, and a password. Keytool manages everything through the Java Key Store (JKS).
keytool -genkeypair -alias client -keyalg RSA -keysize 2048 -keystore clientkeystore.jks -storepass <password> -keypass <password> -dname "CN=<common name>, OU=<organizational unit>, O=<organization name>, L=<city/locality name>, ST=<state name>, C=<country name>"
2.Generate the Certificate Signing Request (for example: 'certreq.csr') file from your Java Key Store as shown below. Be sure to copy the User ID and Password because you will need these to invoke APIs with Two-Way SSL.
keytool -certreq -alias client -keystore clientkeystore.jks -storepass <password> -keypass <password> -file certreq.csr
You now have the Java Key Store file (which contains your private key) and the CSR file.
Certificate (root CA) and the certificate (client cert) to a local folder. You should see both VDPCA.pem and cert.pem in your local folder.
3.Update Java Key Store with Root Certificate and Client Certificate using Java Keytool.
To invoke an API using Two-Way SSL, you must have a client certificate and your root CA in your keystore, since your Java SSL library only accepts one input for all certificates – the keystore. Therefore, you will need to add the certificates downloaded from VDP to the keystore (for example: clientkeystore.jks) that you generated while creating the CSR.
To add a project-specific certificate to the keystore:
1.Add the VDP CA Root Public Certificate to the keystore:
keytool -import -alias ejbca -keystore clientkeystore.jks -file VDPCA-Sandbox.pem -storepass <password>
Note: Replace the < password > above with the actual password that was used while creating the clientkeystore.jks.
Click yes when prompted to trust the certificate option.
2.Add the project specific certificate to the keystore:
keytool -import -alias client -keystore clientkeystore.jks -file cert.pem -storepass <password>
The resulting file, called clientkeystore.jks will contain your private key, your client certificate and your VDP CA root certificate.
Thanks,
Diana
Was your question answered? Don't forget to click on "Accept as Solution" to help other devs find the answer to the same question.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Configuring a Two-Way SSL Keystore Using an Auto-generated CSR
The following steps include examples for context.
1.Place your private key file (for example: privateKey.pem) and your certificate file from VDP (for example: cert.pem) in the same directory. Generate a keystore (for example: myProject_keyAndCertBundle.p12) file as shown below.
> openssl pkcs12 -export -in cert.pem -inkey "privateKey.pem" -certfile cert.pem -out myProject_keyAndCertBundle.p12
Note: The myProject_keyAndCertBundle.p12 is only a placeholder file name. You may choose to name it anything else.
2.If you need a Java Key Store, run the following Java keytool command to convert your P12 file into a JKS file.
> keytool -importkeystore -srckeystore myProject_keyAndCertBundle.p12 -srcstoretype PKCS12 -destkeystore myProject_keyAndCertBundle.jks
3.Run the following Java keytool command to validate the contents of your new JKS file.
> keytool -list -v -keystore myProject_keyAndCertBundle.jks
4.Run the following command to add the root certificate to your JKS file.
> keytool -import -alias ejbca -keystore myProject_keyAndCertBundle.jks -file VDPCA-SBX.pem -storepass <password>
Hi,
With reference to the above portion in the spoiler tag, I have the project certificate and its private key which has been generated by Visa. And for now, I am only interested in the sandbox. From what I have understood of your previous reply, I have created a jks keystore and added VDPCA-SBX.pem and DigiCertGlobalRootCA.cer to it but without the project certificate and its private key.
However, based off the 2 way SSL page Visa has the first command seems to be just adding the project certificate and its private key to a p12 keystore. As a side note, the "-in" parameter and "-certfile" parameter is the same?
openssl pkcs12 -export -in cert.pem -inkey "privateKey.pem" -certfile cert.pem -out myProject_keyAndCertBundle.p12
And then add in the Visa cert (VDPCA-SBX.pem)
keytool -import -alias ejbca -keystore myProject_keyAndCertBundle.jks -file VDPCA-SBX.pem -storepass
But I do not see the CA certificate (DigiCerGlobalCA.cer) being added. Can I confirm that with the resulting jks file (containing privateKey, projectCert, VDPCA-SBX only) I would be able to complete all the necessary client authentication processes when I establish the SSL socket?
And to clear up the terminology:
private key: the file which is only available for download once upon creation of project.
client certificate: the project cert which is available for download beside the username and password portion of the project
certificate authority root certificate: is this DigiCertGlobalRootCA.cer? Or VDPCA-SBX.pem?
As always thank you for your prompt replies!
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @boav_rum,
In this same forum post but previous post thread, I provided steps on Configuring Two-Way SSL Keystore Using Your Own CSR and how To generate a CSR using keytool - Generate a keystore file that contains public/private key pair (for example: 'clientkeystore.jks'), as shown below, using RSA, a keysize of 2048, and a password. Keytool manages everything through the Java Key Store (JKS). Please follow those steps.
In this reply forum post, here are the steps on how to Update Java Key Store with Root Certificate and Client Certificate using Java Keytool, Add the VDP CA Root Public Certificate to the keystore, and Add the project specific certificate to the keystore.
Please see my Java Keytool commands below. After creating your clientkeystore.jks file and the certreq1.csr file. You will need to add the following certificates to your clientkeystore.jks file.
From your project dashboard, download the project certificate with filename cert.pem and place it in the local folder where you have your clientkeystore.jks file and the certreq1.csr file. You should also have downloaded the Visa Development Platform Certificate with filename VDP-SBX.pem and also download the DigiCert Certificate with filename DigiCertGlobalRootCA.cer. Place all the downloaded files into the same local folder that your clientkeystore.jks and certreq1.csr files are in.
Before adding your DigiCertGlobalRootCA.cer file to the clientkeystore.jks file, make sure to go through the Windows Certificate Management steps, so that it is Base-64 encoded X.509 (.cer). I've provided the steps to do this below:
Windows Certificate Management
1.Double-click on the DigiCertGlobalRootCA.crt file to open it into the certificate display.
2.Select the Details tab, then select the Copy to file button.
3.Click Next on the Certificate Wizard.
4.Select Base-64 encoded X.509 (.CER), then Next.
5.Select Browse (to locate a destination) and type in the filename DigiCertGlobalRootCA.
6.Click Save. You now have the file DigiCertGlobalRootCA.cer
Note, I replaced the original downloaded DigiCertGlobalRootCA.cer with the DigiCertGlobalRootCA.cer file that has gone through the Windows Certificate Management steps above.
Now please follow the Java Keytool commands below to add these 3 certificates to your clientkeystore.jks file.
My example below is for Foreign Exchange Rates API but just follow this process for any API that requires Two-Way (Mutual) SSL authentication.
Java Keytool Commands and its Outputs
Microsoft Windows [Version 10.0.15063]
(c) 2017 Microsoft Corporation. All rights reserved.
C:\Users\dtranyee>cd C:\Users\dtranyee\Documents\A Test Project\20190626 Foreign Exchange Rates test1
C:\Users\dtranyee\Documents\A Test Project\20190626 Foreign Exchange Rates test1>keytool -genkeypair -alias client -keyalg RSA -keysize 2048 -keystore clientkeystore.jks -storepass Visa123 -keypass Visa123 -dname "CN=services.visa.com, OU=VDP, O=Visa, L=Foster City, ST=California, C=US"
Warning:
The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore clientkeystore.jks -destkeystore clientkeystore.jks -deststoretype pkcs12".
C:\Users\dtranyee\Documents\A Test Project\20190626 Foreign Exchange Rates test1>keytool -certreq -alias client -keystore clientkeystore.jks -storepass Visa123 -keypass Visa123 -file certreq1.csr
Warning:
The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore clientkeystore.jks -destkeystore clientkeystore.jks -deststoretype pkcs12".
C:\Users\dtranyee\Documents\A Test Project\20190626 Foreign Exchange Rates test1>keytool -import -alias DigiCertGlobalCA -keystore clientkeystore.jks -file DigiCertGlobalRootCA.cer
Enter keystore password:
Owner: CN=DigiCert Global Root CA, OU=www.digicert.com, O=DigiCert Inc, C=US
Issuer: CN=DigiCert Global Root CA, OU=www.digicert.com, O=DigiCert Inc, C=US
Serial number: 83be056904246b1a1756ac95991c74a
Valid from: Thu Nov 09 16:00:00 PST 2006 until: Sun Nov 09 16:00:00 PST 2031
Certificate fingerprints:
MD5: 79:E4:A9:84:0D:7D:3A:96:D7:C0:4F:E2:43:4C:89:2E
SHA1: A8:98:5D:3A:65:E5:E5:C4:B2:D7:D6:6D:40:C6:DD:2F:B1:9C:54:36
SHA256: 43:48:A0:E9:44:4C:78:CB:26:5E:05:8D:5E:89:44:B4:D8:4F:96:62:BD:26:DB:25:7F:89:34:A4:43:C7:01:61
Signature algorithm name: SHA1withRSA
Subject Public Key Algorithm: 2048-bit RSA key
Version: 3
Extensions:
#1: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 03 DE 50 35 56 D1 4C BB 66 F0 A3 E2 1B 1B C3 97 ..P5V.L.f.......
0010: B2 3D D1 55 .=.U
]
]
#2: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen:2147483647
]
#3: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_CertSign
Crl_Sign
]
#4: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 03 DE 50 35 56 D1 4C BB 66 F0 A3 E2 1B 1B C3 97 ..P5V.L.f.......
0010: B2 3D D1 55 .=.U
]
]
Trust this certificate? [no]: yes
Certificate was added to keystore
Warning:
The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore clientkeystore.jks -destkeystore clientkeystore.jks -deststoretype pkcs12".
C:\Users\dtranyee\Documents\A Test Project\20190626 Foreign Exchange Rates test1>keytool -import -alias ejbca -keystore clientkeystore.jks -file VDPCA-SBX.pem -storepass Visa123
Owner: C=US, O=VDPVISACA, CN=VDPCA
Issuer: C=US, O=VDPVISACA, CN=VDPCA
Serial number: 2d1ed295f96ad97a
Valid from: Thu Jul 23 21:27:37 PDT 2015 until: Sun Jul 20 21:27:37 PDT 2025
Certificate fingerprints:
MD5: 86:73:94:83:49:00:9D:82:CF:A0:BD:FE:F2:E3:95:F3
SHA1: A9:30:33:1C:EC:50:7C:71:60:51:4E:03:FF:9E:C1:CA:E6:FE:EC:C4
SHA256: 8D:65:FA:35:59:FD:C3:43:F0:E6:F0:DF:AB:03:DE:49:F3:76:14:20:22:69:C4:B2:56:1A:AC:24:07:7B:C1:F6
Signature algorithm name: SHA256withRSA
Subject Public Key Algorithm: 2048-bit RSA key
Version: 3
Extensions:
#1: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: AF DD 6E B6 A0 4B 9C 79 B9 16 08 62 E6 23 31 10 ..n..K.y...b.#1.
0010: A7 82 EB A1 ....
]
]
#2: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen:2147483647
]
#3: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_CertSign
Crl_Sign
]
#4: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: AF DD 6E B6 A0 4B 9C 79 B9 16 08 62 E6 23 31 10 ..n..K.y...b.#1.
0010: A7 82 EB A1 ....
]
]
Trust this certificate? [no]: yes
Certificate was added to keystore
Warning:
The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore clientkeystore.jks -destkeystore clientkeystore.jks -deststoretype pkcs12".
C:\Users\dtranyee\Documents\A Test Project\20190626 Foreign Exchange Rates test1>keytool -import -alias client -keystore clientkeystore.jks -file cert.pem -storepass Visa123
Certificate reply was installed in keystore
Warning:
The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore clientkeystore.jks -destkeystore clientkeystore.jks -deststoretype pkcs12".
C:\Users\dtranyee\Documents\A Test Project\20190626 Foreign Exchange Rates test1>
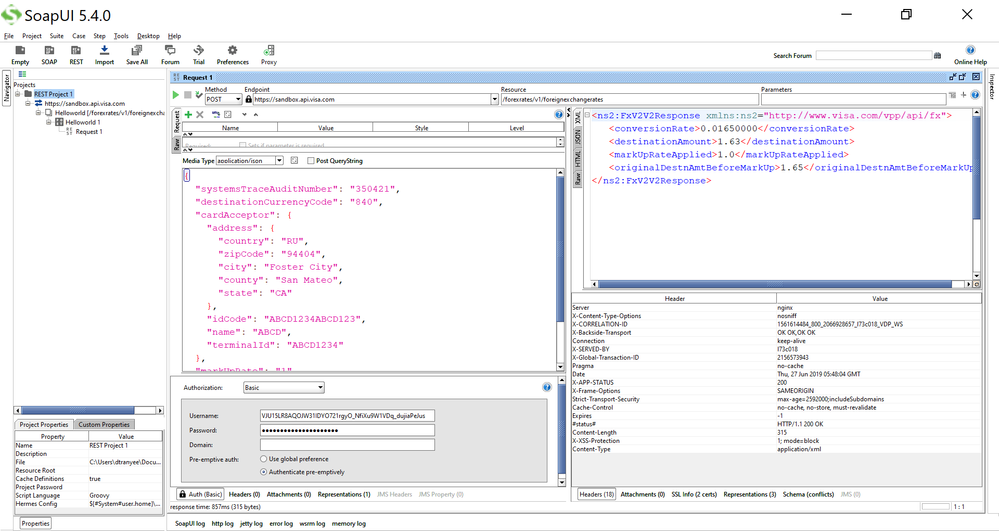
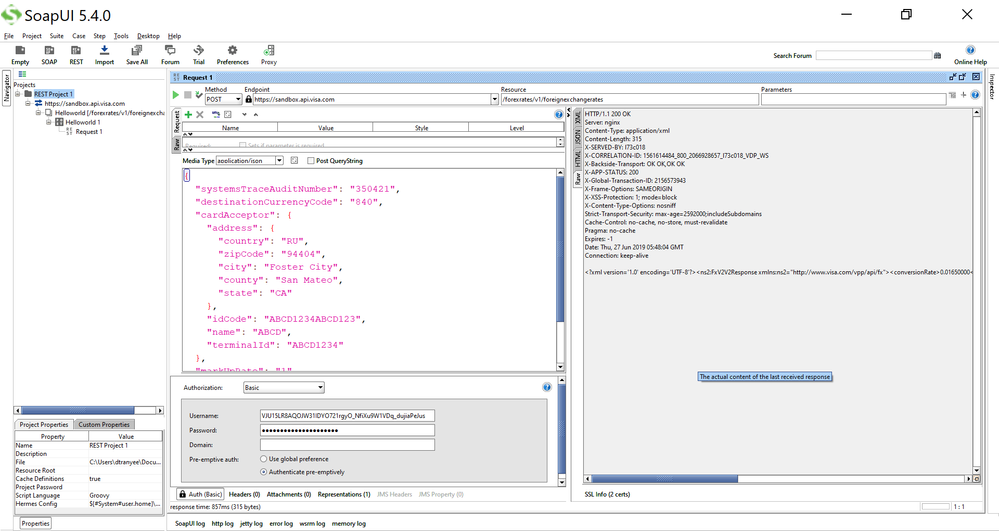
After you add all these 3 certificates, you can start testing in SoapUI and get successful results. Refer to this link on how to setup SoapUI - https://developer.visa.com/pages/working-with-visa-apis/two-way-ssl#testing_twoway_ssl_connectivity_.... Refer to the screenshot above for the successful request payload and its 200 OK results.
@boav_rum, after following all these steps in this forum post, can you please confirm that you are getting successful 200 OK results for an API that uses Two-Way SSL?

