- Visa Developer Community
- Forums
- Two-way SSL & X-Pay Token
- Two-Way SSL, Visa Merchant Screening Service: cann...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ! I am developing an integration with Visa Merchant Screening Service API. I took “Message Level Encryption Sample Code” from the Dashboard page (https://developer.visa.com/portal/app/dashboard) archive and substituted my values with the paths to certificates, request body etc into the test.
When I run it, API returns me HTTP 200 OK and the payload - please see the log below
POST https://sandbox.api.visa.com/vmss/v2/searchTerminatedRequest
keyId: 16a4a980-5edd-4588-881d-94a3cb79088c
content-type: application/json
accept: application/json
x-correlation-id: 337969538796_SC
{'encData': 'eyJhbGciOiJSU0EtT0FFUC0yNTYiLCJlbmMiOiJBMTI4R0NNIiwiaWF0IjoxNjg3MjQ5MDE3NTI2LCJraWQiOiIxNmE0YTk4MC01ZWRkLTQ1ODgtODgxZC05NGEzY2I3OTA4OGMiLCJ0eXAiOiJKV0UifQ.CEqbVeLCLBer5cVOZFb_zZJD0iFNz6n-sNgWHGWKkmZFA6zlprrghbuXwX8ouW_hulvu9MIDfdh8hK7cl3I92X3j1_zC5EUnh2kAZYyX3sIJCZFf8JbZ8LFigpxk06uLL1CXZgtk0C8Ajk3pwZUdLXRPA6BUT_AF9QKLDAj-mBjJql4mrdnnsYwbfukvyi2f_9gDpezSUzLuYniBDrOqU1UA_-u3h61FmIGSkDJ4mA_4L_-QCIHBu3fSs3rzarXueqIVJCYFrMzYSDMtznMqttLyK9QBbGhCUwEN7mGXGHRzSsMGwIShMnPRzkrgWhZt5I7n4AVMKd8frG2_0RIqIQ.lqYrMmD8kA9wW6Gj.3BiXlLx-ueo9I4AfYZ30rSj9bR7KmgXoUfHrV3nbhuIwv0iJ4OO7d9VzdG9NDu66q6FYjaR9Y-kTnMeXfBsccbX5SzVcj-SkQ1pXl48wP6DVEW6I3F9ccgoR7J-1TBEhlFOxjFfrQuydokXk8xKCgb8Yfti8YILm3hQ5c_wAisfCB2e27wug8gu60N7eORTCyt8rbD5ZWayOikQaqRn0rQ8mkgWidNm9UTeO__MzXO-jWzONMKj9_0VUCWik3Jr2WNjKkSKKqAPFyP2WcT3NcQXCKUN5pWF7ZzJ2WFhiK99nv98GaWtL6A3DU5Q4cxgT_exCECQk9CplfvHNKRIxTbPYnDcNN9Cmt1P_kB20xCIVTMMAbujPuO5BFMum8_DKlIvmZ4kq9pLFDf7q6mT78Ngze-9aafkunjZilEvzSh9g1cGR1Jht8wIFZSK7XtHQAMVWYfH9Kc_oy2ZX9umZnj92auo68BuvH_gFBw0sWcA9nac9hmYoHyoC5tU9vG7qPaEUg3LMV3C6TtbTXVoMo68RDtKvv7drf-2w8L_UPQ49lyzFUeIwCfsp6jvCVqur1_y53mvX_08Nr7d39ZoekvwcJmLKvb-Gby2NCtLqm8dsCldYvu8aBPFaw-ju5qst08uiPB6OhO31NInsTkGkugliYbUG7v0_28OlhfXA3V1TtsoLtlB8xSZiFVbYqoWp4Zk-HFNkU6bjarU-7MdzuveqlaKK6essu1wxlpQkEdfJrmNttp8wMQN_QAi3UE9WVMgYtEBKvRteQXnKQyvnJNqjYTxYFgZqbYeBQig2R3pk_Rv62tIS9uzTCVIw8buC3M64ZZBKKmWwFsggND3bO_MgTibTj3Ocndg4YJD9PCoBUdJVZujOl20M4hgl4GkVgRyJBQ.oOc2YkTGCGhBs8Saa4IKsQ'}
Response:
Code: HTTP 200 OK
Server: nginx
Date: Tue, 20 Jun 2023 08:16:58 GMT
Content-Type: application/json
Content-Length: 659
Connection: keep-alive
X-SERVED-BY: -5c8c48b66-2q5
X-CORRELATION-ID: 1687249018_151_1668396478_-5c8c48b66-2q5_VDP_WS
response-message-id: 6e3de805-3d5d-4dee-b297-32e9a779609f
response-message-ts: 2023-06-20T08:16:58.379779128Z
X-AGS-Request-ID: v3:8651:sandbox:73c010:0f4b6495cb113a4fd4094ff8ba0fafab
X-APP-STATUS: 200
Cache-Control: no-cache, no-store, must-revalidate
X-Frame-Options: SAMEORIGIN
X-XSS-Protection: 0, 1; mode=block
X-Content-Type-Options: nosniff, nosniff
Strict-Transport-Security: max-age=31536000;includeSubdomains, max-age=31536000;includeSubdomains;always
Pragma: no-cache
Expires: -1
Content-Security-Policy-Report-Only: default-src 'self' https://*.v.me https://*.visa.com;script-src 'self' 'unsafe-inline' 'unsafe-eval' https://*.visa.com https://*.v.me;img-src 'self' https://*.v.me https://*.visa.com https://*.unica.com https://ad.doubleclick.net;style-src 'self' 'unsafe-inline' https://*.visa.com;object-src https://*.v.me https://*.visa.com data:;report-uri /logging/logCSPReport;
X-Content-Security-Policy-Report-Only: default-src 'self' https://*.v.me https://*.visa.com;script-src 'self' 'unsafe-inline' 'unsafe-eval' https://*.visa.com https://*.v.me;img-src 'self' https://*.v.me https://*.visa.com https://*.unica.com https://ad.doubleclick.net;style-src 'self' 'unsafe-inline' https://*.visa.com;object-src https://*.v.me https://*.visa.com data:;report-uri /logging/logCSPReport;
X-WebKit-CSP-Report-Only: default-src 'self' https://*.v.me https://*.visa.com;script-src 'self' 'unsafe-inline' 'unsafe-eval' https://*.visa.com https://*.v.me;img-src 'self' https://*.v.me https://*.visa.com https://*.unica.com https://ad.doubleclick.net;style-src 'self' 'unsafe-inline' https://*.visa.com;object-src https://*.v.me https://*.visa.com data:;report-uri /logging/logCSPReport;
{"encData":"eyJjdHkiOiJhcHBsaWNhdGlvblwvanNvbiIsImVuYyI6IkExMjhHQ00iLCJhbGciOiJSU0EtT0FFUC0yNTYifQ.Sb7YplNpUf5EWHJ5fvD5kIK1yxfa6Kpk_ik3SJ27O_QV7q7t58rtpehIdAlFeu668gh02MtPXmLiaZhf2J67RMaakjkvB9nSmv-f-yfYpaNlFdTk7UzVzFgMVXH6Jg62GgS7T1h_mvNUTQpGH_2vFuJdYiFhnT0KaRSvmFyJz4Hjqdlhz4L2oFvul_bYViYM5EKJgvaRGvUdwPBniBVz_BusuOFdu5X_7nn0JSr-Ph0bwEcc9cFIpP-tYKQD1eSSDlNelrQE0V9p4hMkC0Jx9a7xOhkRvGJFBh3EWOUTqBs4PHQd9qUOPVqcul8xXAf35GBy939RHAOH9ukTBJb80A.UiPrLN4w0Z0vO2Ru.Ec0r-wVmHfWxGdNNIWupZwz1zXicmdxQKXYQh9Ot9ghyFfnggCh1tRgrSW5MG21zptorW7wnZX3fLLQN9H6kKpqiNPRg-2AKntNPm04XfVXIDWIFBDPdADHwXvrNMc_e4KhABIxxIGZP6K25w7QmRGQWdR8s9y0Iwvj8bPFx7hHbZxw.YOLSOspwouhO7PWl7HvfxA"}
Ran 1 test in 1.142s
FAILED (errors=1)
Error
Traceback (most recent call last):
File "/Users/const/projects/nmpa-dnet/current/mle_sample/test/test_mle_oct.py", line 58, in test_push_funds_transactions_mle
decrypted_json_response = json.loads(jwe_encryption_util.decrypt_jwe_token(json.loads(response_body)['encData'], jwe_encryption_util.import_key(decryption_key)))
File "/Users/const/projects/nmpa-dnet/current/mle_sample/utils/jwe_encryption_util.py", line 31, in decrypt_jwe_token
jwe_token.deserialize(encrypted_payload, decryption_key)
File "/Users/const/projects/nmpa-dnet/current/mle_sample/venv/lib/python3.9/site-packages/jwcrypto/jwe.py", line 546, in deserialize
self.decrypt(key)
File "/Users/const/projects/nmpa-dnet/current/mle_sample/venv/lib/python3.9/site-packages/jwcrypto/jwe.py", line 469, in decrypt
raise InvalidJWEData('No recipient matched the provided '
jwcrypto.jwe.InvalidJWEData: No recipient matched the provided key['Failed: [TypeError("object of type \'NoneType\' has no len()")]']
And it failed to decrypt the payload due to
jwcrypto.jwe.InvalidJWEData: No recipient matched the provided key['Failed: [TypeError("object of type \'NoneType\' has no len()")]']
Could you please help to figure out what is wrong and what is the cause of this ?
Solved! Go to Solution
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Two-Way SSL, Visa Merchant Screening Service: cannot decrypt response
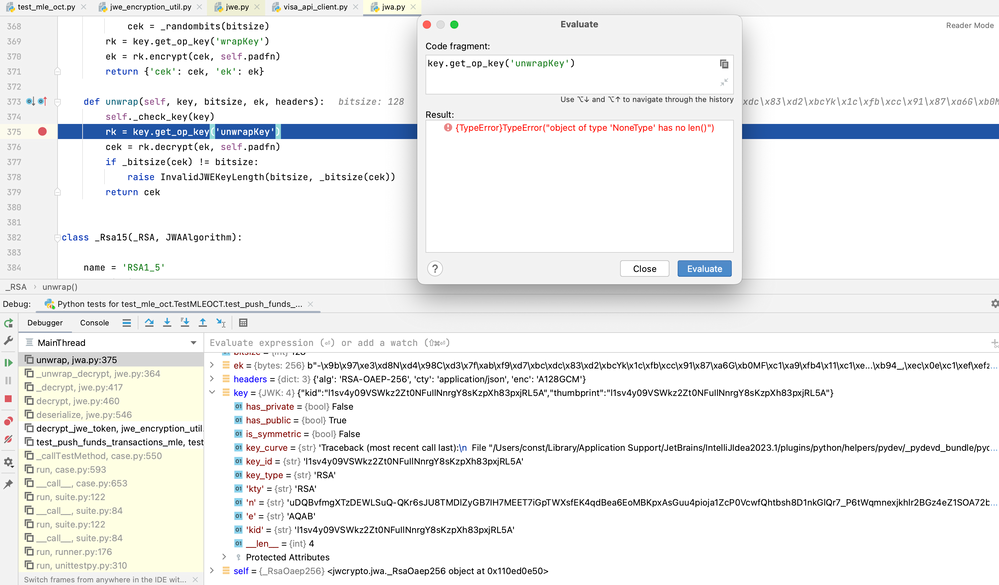
In debug session it fails at this point:
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Two-Way SSL, Visa Merchant Screening Service: cannot decrypt response
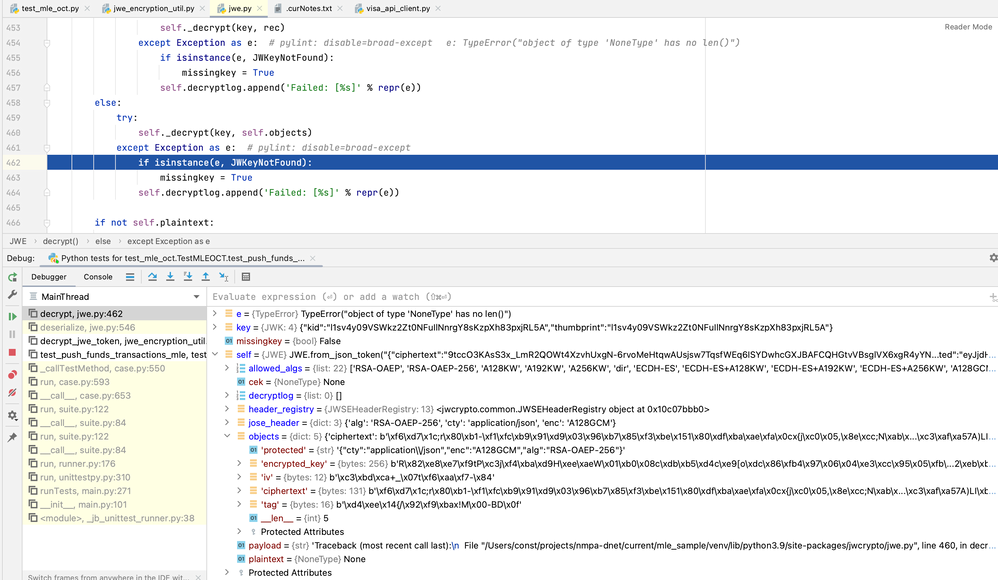
Actually, this is the final point where it fails:
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Two-Way SSL, Visa Merchant Screening Service: cannot decrypt response
Hi @kkachanouski,
Great to hear the problem is fixed and what the solution is. Enjoy the rest of your day!
Thanks,
Diana
Was your question answered? Don't forget to click on "Accept as Solution" to help other devs find the answer to the same question.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content