How to test and troubleshoot APIs with the Visa Developer Center Playground
We feel that the Visa Developer Center has come full circle since launch in 2016. It hosts many APIs...
Visa upgraded our security system that authenticates a project in all environments to prevent vulnerabilities.
Why should you care?
This means, in order for you to continue using your project in our environments, you will need to upgrade to our latest security version TLS 1.2. Older TLS versions are vulnerable to security breaches. Please upgrade your TLS version to 1.2.
Your application will stop working if you continue to use any version lower than TLS 1.2 beyond the dates mentioned below:
What is TLS?
TLS stands for “Transport Layer Security.” It provides privacy and data integrity between two communicating applications. It is used to authenticate one or both applications, and protect the confidentiality and integrity of information that passes between them.
Overtime, different versions of TLS have been released; TLS 1.2 was released in August 2008, it addresses many vulnerabilities identified in the earlier versions.
What happens if I don’t upgrade?
PCI DSS standard version 3.1 was retired in October 2016 and makes all older TLS versions (e.g. SSL v3, TLS 1.0, TLS 1.1) non-compliant. The standard requires the new TLS requirement to be implemented.
Visa has decided to proactively implement PCI DSS guidelines to provide greater protection to our clients. If you don’t upgrade your TLS version beyond the cutoff date notified to you by developer communication, you will no longer be able to use your projects in any environment.
If you have any further questions you can always email us at developer@visa.com
How do I find which version of TLS I am using?
getProtocol() method in SSLSession will provide the details of TLS version you are using.
Please refer to the Java documentation for the details.
How to Upgrade:
Application
If your application does not automatically pick up TLS 1.2 version you need to explicity provide that as an override.
For example, for SoapUI tool, set -Dsopui.https.protocols property to TLSv1.2 refer to appropriate documentation on how to set SSL version for your application .
Please refer to compatibility guidelines for the most popular Languages and Libraries:
Java 1.5 and below does not support TLS 1.2
In Java 1.6, TLS 1.2 is not supported in Oracle public updates. It is supported in the business edition starting Oracle java version 6u115 b32.
In Java 1.7, TLS1.2 is supported. But it needs to be explicitly enabled by selecting the enabled protocols while creating the SSLSocket & SSLEngine instances.
Enable TLS 1.2:
Add ( -Dhttps.protocols=”TLSv1.2″ -Djdk.tls.client.protocols=”TLSv1.2″) to Java command line arguments which is used to launch client application. This will allow turning off support for TLS 1.1 and below on the server side completely and will support TLSv1.2.
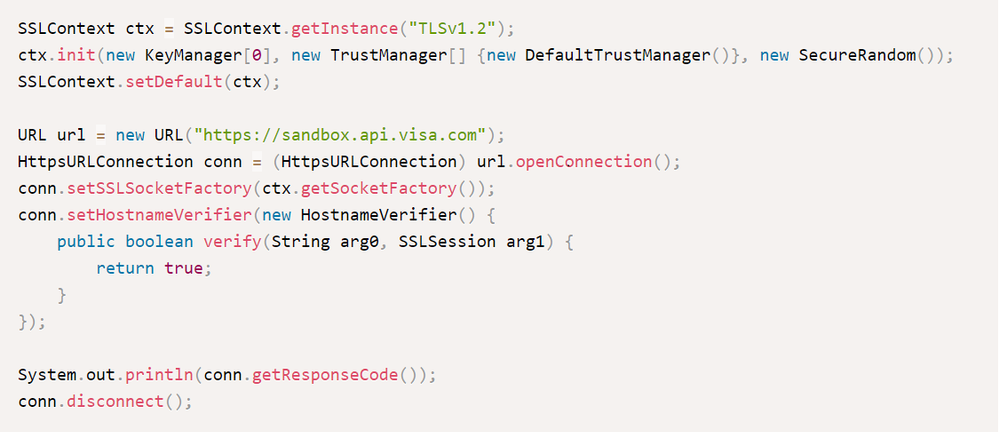
Java client with basic URL connection:
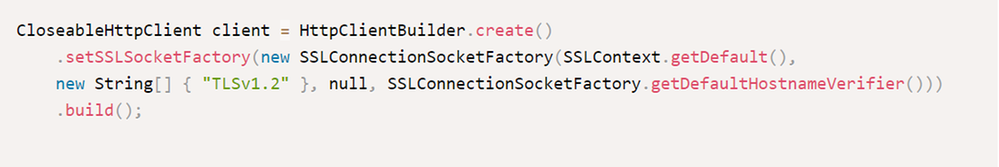
Java client using Apache Http Components client:
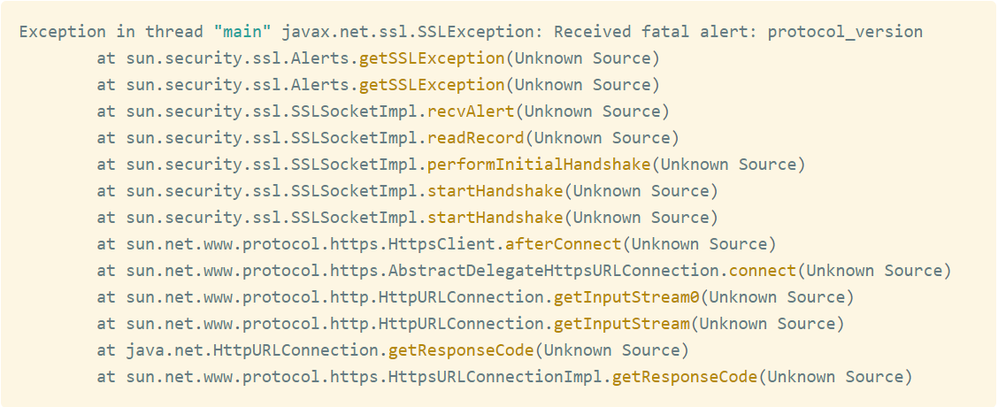
Exception in case of incorrect TLS version would be:
Please refer https://blogs.oracle.com/java-platform-group/jdk-8-will-use-tls-12-as-default for more details.
Ruby uses the system OpenSSL. OpenSSL v0.9.8 will no longer work, but later versions work without any changes required.
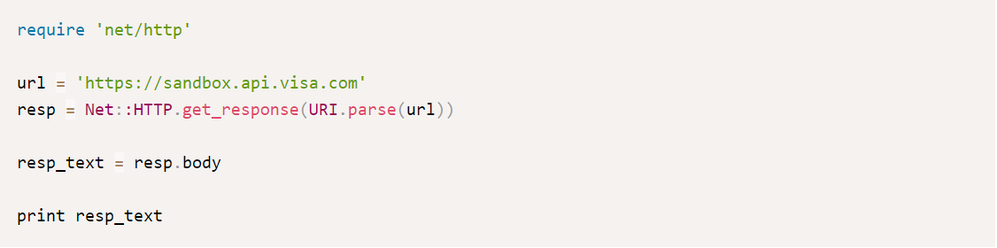
OpenSSL v1.0.1 supports TLS 1.2 by default. With Ruby 2.0, you can test the connection with this script:
Exception in case of incorrect TLS version would be:
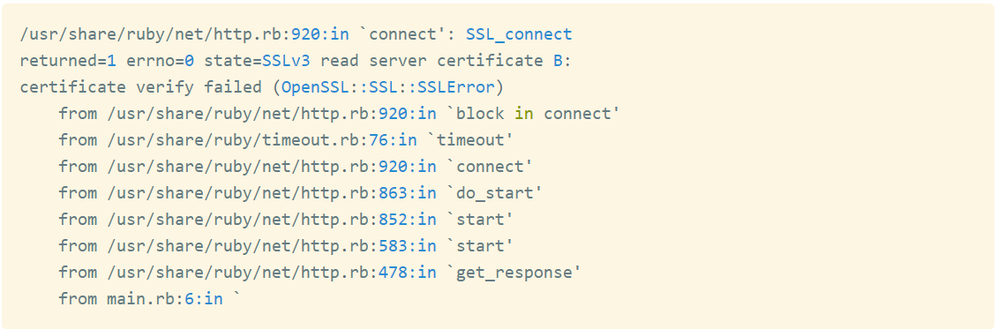
Please refer https://github.com/ruby/openssl for more information.
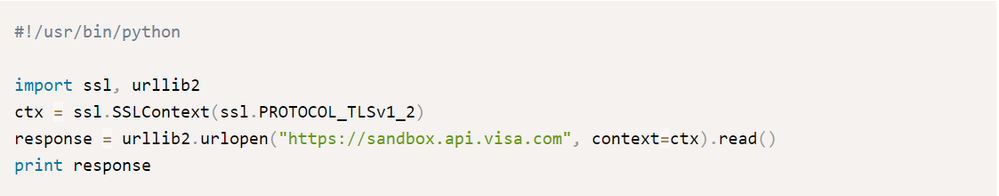
Just like Ruby, it is better to update the OpenSSL version. You can test the TLS connectivity with the following code snippet.
Exception in case of incorrect TLS version would be:
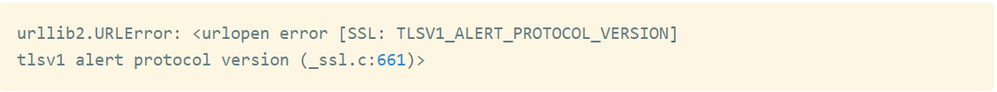
Please refer https://docs.python.org/2/library/ssl.html for more information
Curl supports TLS1.2 starting 7.34.0. Please use the following command to test the connection:

If you have any further questions you can always email us at developer@visa.com
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
We feel that the Visa Developer Center has come full circle since launch in 2016. It hosts many APIs...
In this developer guide, we will show you how to test Message Level Encryption (MLE) enabled APIs us...
First time to the Visa Developer Center? Watch this tutorial to learn where to find the Visa APIs th...
Watch the recording of my How to Run a Visa Direct Transaction using Python webinar as you follow al...